The Power of Endpoint Security: Protecting Your Business in the Digital Age
Brian Snow • May 1, 2023

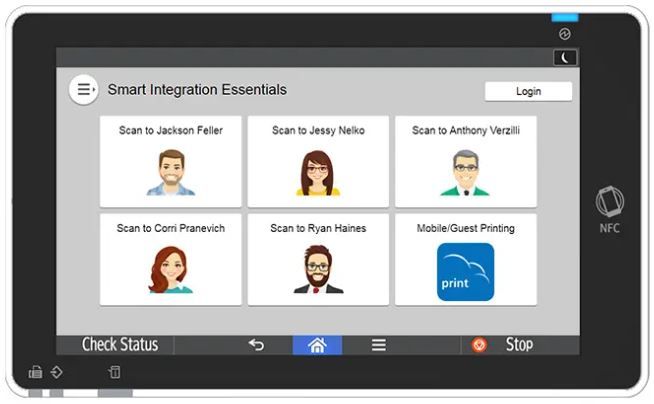
State and local government agencies face unique challenges in managing complex IT environments, ensuring security compliance, and optimizing productivity—all while keeping operational costs under control. Whether you're in law enforcement, finance, or general administration, Toshiba's Elevate Sky® cloud-based solutions offer robust tools specifically designed to streamline processes, enhance document security, and optimize your print and workflow management. Cloud Integration Tailored for Government Efficiency Today’s hybrid work landscape demands secure access to critical information anytime and anywhere. Toshiba’s Elevate Sky® cloud solutions directly address this by transforming traditional document handling into seamless digital workflows. By integrating Toshiba’s multifunction printers (MFPs) with popular cloud storage services like Microsoft® Office 365®, Google Workspace™, Dropbox™, and Box™, government workers gain unprecedented flexibility and collaboration capabilities. Key features include: Direct Scanning and Printing: Easily scan documents to and from cloud platforms, securely integrating physical and digital workflows. Automated Document Workflows: Elevate customizes workflows on the MFP interface to match your department’s exact needs. Universal Cloud Print: Toshiba MFPs natively support Microsoft® Universal Print, eliminating on-premises print servers and software, ideal for government agencies with dispersed locations. Enhancing Productivity and Reducing Operational Costs Efficiency and cost optimization are critical for agencies facing tight budgets and stringent accountability requirements. Toshiba’s Elevate Sky® Print Management consolidates print operations into a centralized, cloud-native platform that dramatically reduces overhead costs and IT burdens. With features such as automated printer management, a single universal print driver, and zero-touch deployment, agencies benefit from significant savings in time and resources. Notable benefits include: Reduced IT Overhead: Automate routine print management tasks, freeing IT staff to focus on strategic initiatives. Transparent Cost Management: Detailed reporting identifies cost inefficiencies and wasteful printing practices. Sustainable Printing: Centralized management reduces print waste and enhances environmental responsibility. Unmatched Security for Sensitive Government Data Government agencies must adhere to strict security protocols to protect sensitive data and comply with regulations like HIPAA, GDPR, and Zero Trust principles. Toshiba’s Elevate Sky® solutions deliver exceptional security features that protect your print and digital environments: Robust Authentication: Multi-factor authentication and secure PIN releases ensure only authorized personnel access sensitive documents. Encrypted Data Communication: All communications between Toshiba devices and cloud solutions utilize high-grade encryption (TLS1.2 or higher). Comprehensive Audit Trails: Detailed activity tracking provides full accountability and compliance assurance. Proactive Management and Predictive Maintenance One of the standout features of Toshiba’s Elevate Sky® is the proactive and predictive approach to device maintenance. Leveraging AI-driven analytics, Elevate Sky® Predict anticipates device failures before they occur, minimizing downtime and maximizing productivity. Government agencies benefit significantly from uninterrupted operations and reliable service delivery. Additional proactive features include: Real-time Diagnostics: Quick issue detection and resolution without needing onsite visits. Fleet Management and Optimization: Centralized visibility across your entire fleet of devices for easier management and policy enforcement. Simplified Procurement with Elevate Sky® Commerce Elevate Sky® Commerce provides government purchasing agents a streamlined, secure digital storefront to procure print-related products. Agencies enjoy the convenience of a personalized, user-friendly shopping experience, hassle-free ordering, and transparent tracking and delivery. Benefits for procurement officers include: Secure, Passwordless Access: Safe and simplified access to procurement resources. Customizable Profiles: Easy management of organizational procurement preferences and history. Flexible Payment Methods: Supports purchase orders and a variety of electronic payments, ensuring compliance with government purchasing standards. Trusted by Governments, Powered by Toshiba Toshiba’s longstanding commitment to excellence, security, and innovation makes it an ideal partner for government agencies at all levels. With solutions tailored specifically for public sector needs, Elevate Sky® provides unmatched efficiency, security, and ease of use, helping government decision-makers achieve their goals without compromise. Discover how Toshiba’s Elevate Sky® solutions can transform your agency’s operations today. Connect with a Toshiba expert to learn more. Call today: 850-222-2308